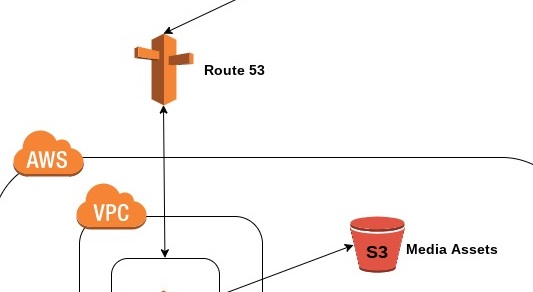
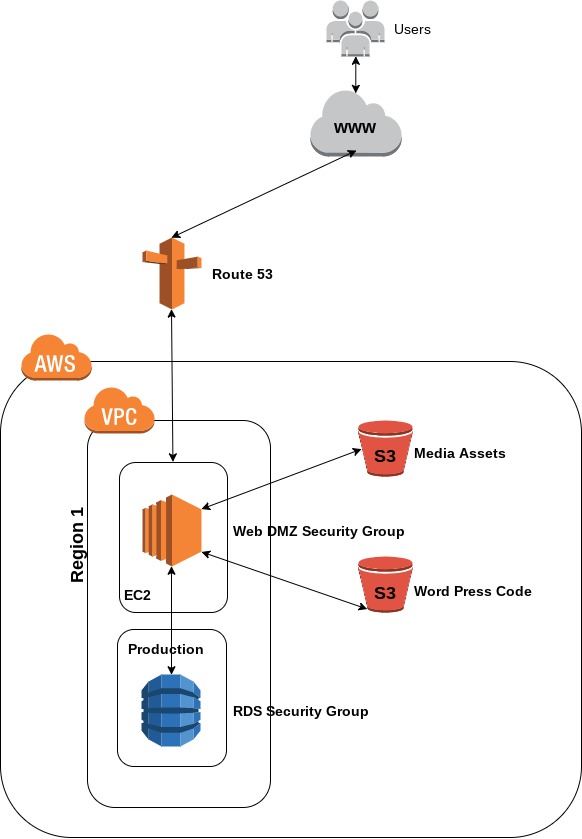
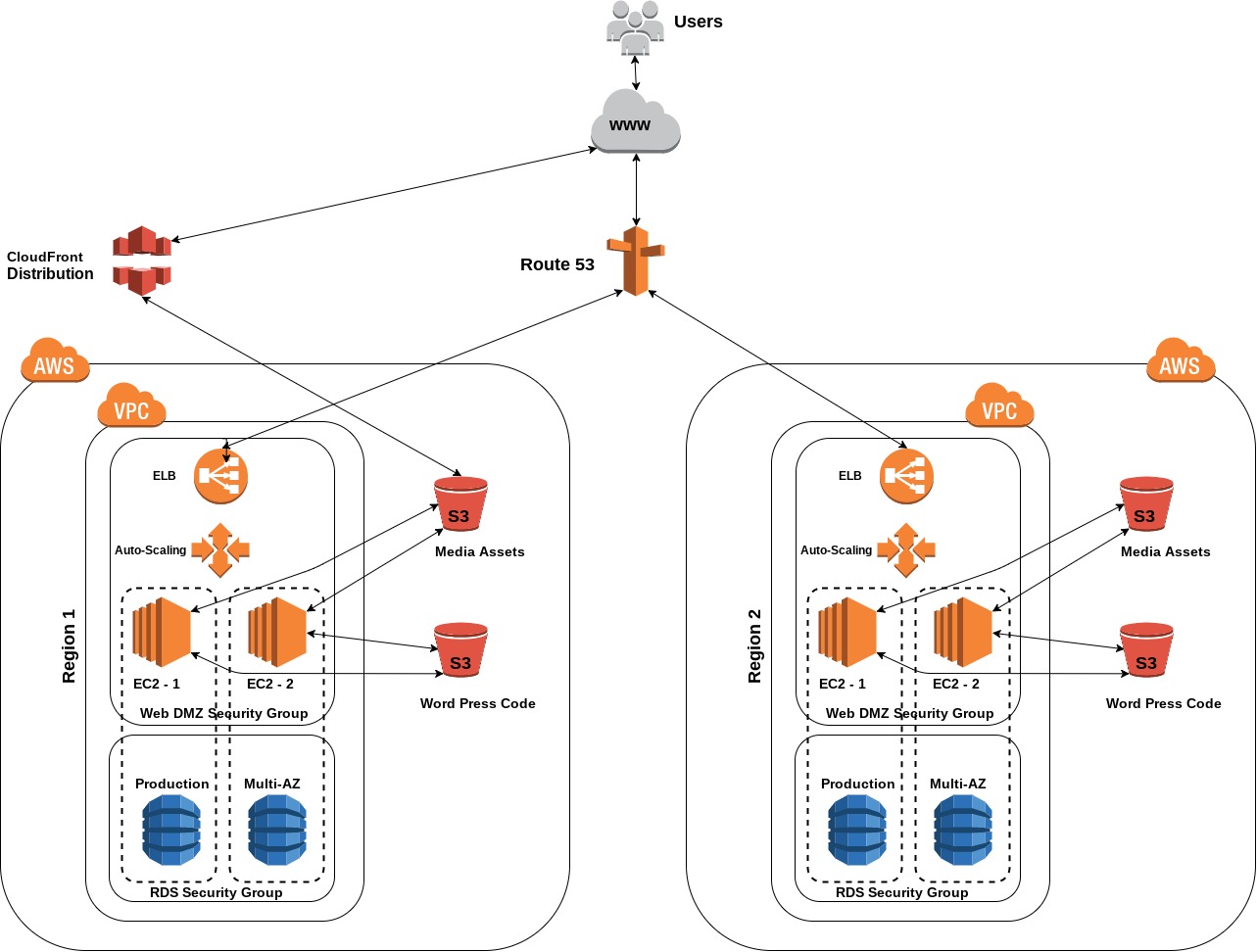
Infrastructure as code (IaC) is now somewhat of a necessity for a Network Engineer in 2024, and if you think about it, it makes perfect sense. With more and more workloads moving to cloud platforms why would you waste time in the GUI when you can code your environments to deploy, replicate them with ease for Test and Pre-Prod, amend when required and always have a as-is state view – how it should look, written down in code!
The tools I am using to embark down this rabbit hole are (I’m on a Mac);
- HomeBrew – a great package manager for MacOS.
- Terraform – This was installed via HomeBrew.
- AWS CLI – As above, HomeBrew.
- Docker Desktop – if you want to create code for automating Container creation/deletion etc as another
- Import AWS IAM Access Keys to AWS CLI
- A Code Editor – I like VSCode because it’s free, but also because there are extensions for many programming languages, that help greatly.
Building the environment

Install of HomeBrew. I ran the curl code on the Homebrew website directly into a Terminal session window. Just make sure to watch out for the additional steps at the end – I missed them first time.

Install Terraform. Homebrew on OS X instructions on developer.hashicorp website – obviously, if your OS is different choose the option that suits.
Install the AWS CLI. I ran the Command Line Installer (Terminal) from the AWS CLI install guide. Again, depending on your flavour of OS, choose accordingly.

Extra! Install Docker Desktop. If you’d like to deploy Terraform for spinning up Docker containers too, I’ve found Docker Desktop to be great. Grab the relevant version here.

Import AWS IAM Access Key Credentials. Note: make sure to download the AC file and store it somewhere secure (key is only available at time of creation!) – or look at utilising Roles (short-term access). This import action permits Terraform to authenticate against the relevant Provider – AWS in this instance. Alternatively run an aws configure once the AWS CLI has been installed to input your access key credentials, which will provide the AWS CLI the relevant permissions to make AWS API calls.

Code Editor. VSCode tends to come out top of many a chart, therefore I went this this, but there are plenty of others to chose from so see which you like – e.g. Sublime Text, NotePadd++, Espresso (Mac).
Once that’s in place you can launch VSCode and open up a terminal window to create your AWS working directory. Note: Each Terraform configuration must be in its own working directory, i.e. AWS, Docker, GCP, Azure.
Within your Terminal window, you can make a new directory to work from.
mkdir terraform-aws
Then navigate into your newly created directory.
cd terraform-aws
Create a new file, which will be used to create our Terraform configuration.
touch main.tf
Then edit this file to begin building out your code. Note: Other text editors are also available.
nano main.tf
Once the directory is created I open the folder within VSCode so I may write code from within the apps editor as opposed to the more clunky, but adequate, terminal window. File > Open Folder > local directory created above. This will then open in the left Explorer pane. For added quality of life you can install some beneficial extension such as Hashicorp Terraform, Terraform and Terraform Autocomplete.
Now we have our environment set up we can now start running terraform code to build out AWS and/or Docker containers. In Part 2 we’ll look at;
- Building out our code in the main.tf file
- Initialising the new configuration to pull down the relevant Providers
- Format and Validate our config
- Create the infrastructure!
Thanks,
Ish